Blogs & Opinions 28.10.2025
CISO ‘How to’ Without the Bull: Mastering Threat Intelligence
CTI doesn’t have to be expensive or time-consuming.

Blogs & Opinions 28.10.2025
CTI doesn’t have to be expensive or time-consuming.
Cyber-threat intelligence (CTI) takes many forms, and the whole topic can mean different things to different people. Let’s define the discipline and highlight some quick wins…
One of the most valuable ways to understand the topic is through the RAF’s intelligence-collection framework. It posits the following: direct, collect, process, analyse, and disseminate. The CTI community has widely adopted this framework. It describes the process of collecting threat intelligence, transforming it into useful information, and passing it to a team that can act on it.
“Intelligence provides data. Analysis of this data can turn this into actionable information”
Intelligence provides data. Analysis of this data can turn this into actionable information. The key is knowing how to use multiple sources of information to take the correct action. The critical step I’ve seen many miss when applying this cycle to CTI is the risk analysis that comes first, along with the actions that must follow.
Risk analysis: What risk are you trying to reduce? If you need early warning of vulnerabilities in your tech stack, or want to know whether your suppliers have suffered a breach, the type of threat intelligence investment will be very different. Often, threat intel is a very specific solution for a particular risk or use case.
Follow-on actions: You must be able to do something with the information, quickly and easily. For example, being told that 100 of your staff have credentials on a breach list being sold on the dark web is essentially pointless. Breach lists are sold and resold over and over again. And often, this list is full of people who have left the firm or changed their passwords since the credentials were first breached years ago.
CTI is usually broken into three varieties:
Tactical – The “what”, aimed at the security operations centre (SOC), threat hunting and incident response (IR) teams. They use tactical CTI to set blocking rules (e.g., specific IPs on a firewall or IPS) and to tune alerts within the SIEM based on specific IoCs and TTPs. These are often very short-term measures.
Operational – The “who” and “where” (TTPs). This is more aimed at understanding APT-level threats, which you need to adjust your security tooling and posture to counter. These include vulnerabilities currently being exploited that require rapid patching. Operational CTI focuses on the medium term.
Strategic – The “why” and “how”. The high-level, big-picture details about threats to your organisation and the threat landscape. Strategic CTI can inform strategy and roadmap to ensure they’re aligned with business risk. Threats at this level might be used to adjust risk scorings. It focuses on the long term.
The information needed to feed tactical, operational and strategic CTI will come from different sources. Trust Groups or ISACs, alongside open source information, can shape the strategic picture. There are many sources of vulnerability intelligence for operational CTI. And research on TTPs and IOCs related to different attack groups is readily available at the tactical level. If your risk profile warrants it, vendors can help expedite the collection of this information.
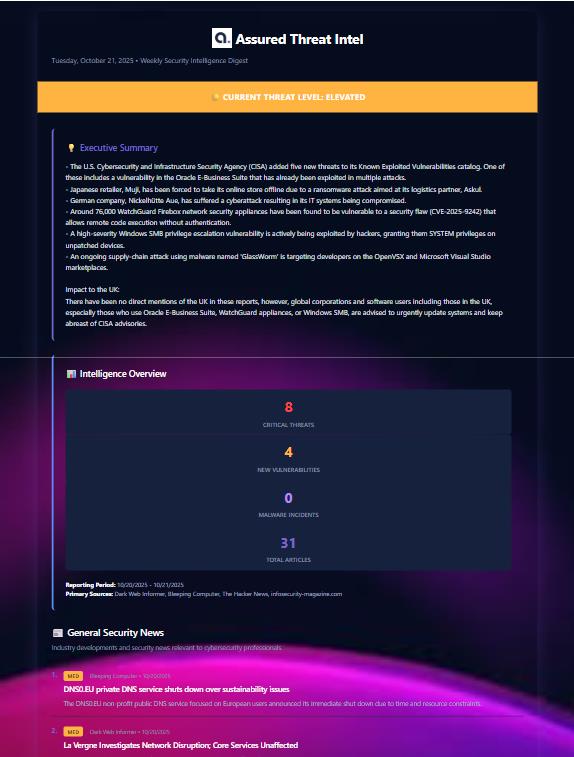
Pricing for CTI solutions can come with a significant premium, which is particularly hard to swallow given that it’s all open-source information. The vendors worth considering are those that can demonstrate historical data from last month/year/decade that they saw before you did, and that would have impacted your organisation. Otherwise, try a few open-source RSS feeds and APIs, pulled into a Slack or Teams channel, or formatted into an email via a cheap automation tool(e.g., N8n). Below, you can see an example of this in action at Assured.
You could harness 80% of the value of a CTI tool for just 2% of the cost. How? By focusing your collection efforts on the RSS feeds that give you the best information, collecting this via a channel or email, and analysing it to filter what is useful. Next, process this information by presenting it at your morning discussion and disseminate the update with clear recommendation actions.
Imagine how long this would take: we’re talking less than 10 minutes of reading a day. This way, you can avoid carving off a section of someone’s role or hiring a new person. See the example below, which arrives every day at 6am and is purely a collection of open source feeds. It’s free, easy and valuable.