
Blogs & Opinions 09.01.2025
CISO “How to” Without the Bull: Cyber-Risk Management (Pt 1)
Where to start and what’s good enough?

Blogs & Opinions 09.01.2025
Where to start and what’s good enough?
There are many risk management frameworks out there and pages upon pages describing them. Just consider the following jumble of letters: OCTAVE, FAIR, IRAM2, ISO27005, NIST and ISC2. This isn’t even considering threat modelling methodologies such as STRIDE, DREAD, Trike, PASTA, Vast, etc.
There are commonalities amongst all these approaches. They all look at assets, threats, impact, likelihood and mitigations. The more you pick them apart, the more you’ll see what they share in common. By all means, explore them all and build your risk process as thoroughly as your resources allow. However, be warned that risk can fast become an industry in itself within the business.
The challenge is not every business knows where to start. Or more likely, they don’t have a large risk team, particularly SMBs with low levels of enterprise risk management maturity. The upside is that the process outlined below is a fantastic opportunity for the cyber risk team to become the ultimate “horizontal” across your entire organisation – opening all the doors as a supportive risk and resilience expert.
Bear in mind that this blog is aimed at starting from a greenfield site, and of course pick out the bits you find useful. Intentionally, avoiding many of the risk framework headings (identify, assess, select controls, etc) which are high level, we’ll delve into a useful level of detail with the following steps, which we’ll expand upon as we go through this blog in two parts:
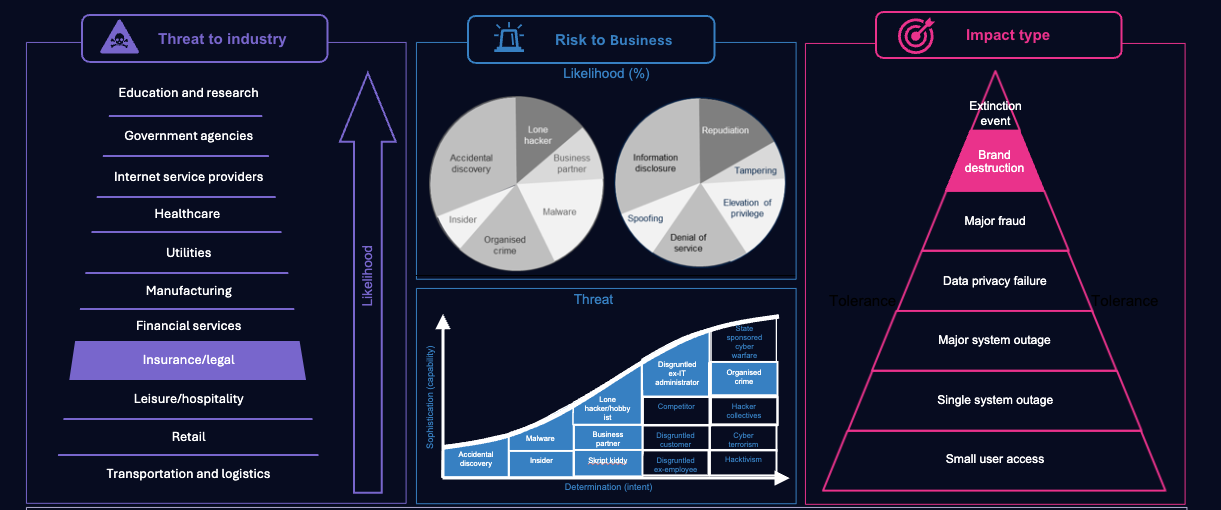
It’s worth considering the threats to your business to get a feel of how secure you need to be. From this point you can decide how big the risk mitigations should be and how much investment in your cybersecurity programme is going to be needed, and in which areas. This can be cracked in a very short amount of time without over-investing.
A worked example (right) shows the relative threats to business industry types, the types of threat which may be expected and the amount of impact the business can tolerate. Using the diagram, select your industry, change the cheese slice sizes and select the determination/sophistication to fit your likely threats, before defining as best you can where your threshold sits.
You may now have a feel of how secure you need to be. Now it’s time to identify which assets are most critical to your business (business critical assets or BCA). Frameworks like to catagorise everything as a type of asset – from people to databases – however I find an ‘information risk’ approach more difficult than focusing on the assets that host them. This is because information moves (we’ll explore information flows later) and additionally, it’s a much longer and more difficult process to find the information owner compared to an application owner. An information owner can also end up being lower in the organisational hierarchy. So, focusing on applications and IT-related assets lets us find an accountable owner for each as we go, which will make the risk ownership conversation later a lot easier
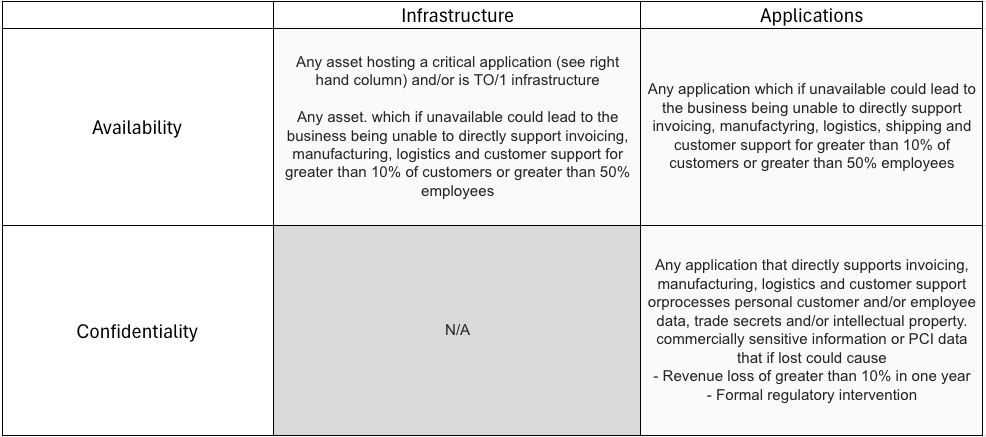
So, how do you find your BCAs? By all means use a version of the example (left) to help identify what is actually critical – in the context of the “availability” and “confidentiality” of the asset.
They reference “information” heavily, so we don’t omit its importance. And those who know the CIA triad, will notice I have skipped “integrity” to keep the process as light as we can make it. Walk the floors, meet everyone, build your understanding of businesses processes and people, to give you a top-rate list of your BCAs. This business enabler approach will also have the positive side effect of building relationships and people opening up to you with their challenges, risks or even useful examples of security friction they experience and you can help address.
You now have an organisational risk profile and a set of critical assets (BCAs). We now need to ensure all our cyber-risk work is tied to the business. If your business has an enterprise risk register, I encourage you dovetail into this. However, it’s likely that you’ll be leading the business down a path of risk management with your cyber risk capturing.
Aligning with the business is extremely important and demands a language they understand. For this, I prefer three tiers, plus any further ineffective controls. This stops the risk register becoming overly complex. These could be as follows:
There is a choice as to whether you explore around the business to capture Tier 3 risks as you go (bottom up) or you pick a framework such as ISO27001 or NIST CSF and create risks based on the failure of their clauses or controls; rewording each clause that is applicable (top down).
“I find an ‘information risk’ approach more difficult than focusing on the assets that host them” Nick Harris
The bottom-up approach has better business engagement, but it can quickly get out of hand as so many risks are captured and you have to ensure you don’t miss any areas. The top-down approach allows you to cover all areas and provides a finite number of risks.
I favour a combination of both top-down and bottom-up approaches. Top down for function risks and bottom up for application risks (which are which, i explain next). But we have now caused our first problem: how to rationalise the two and relate this to the critical asset identification work? My approach at this stage is to break into two risk registers: one functional risk register of top-down risks and another for critical apps.
Application risks (bottom up): Take your BCA list of what is what is critical and, very likely a set of less critical business applications. This list will become your application risk register, and we’ll take a slightly different approach to mitigating these in a later section. At this stage, exchange notes with IT (if you haven’t already) to share your list of critical apps. It’ll really help your service desk with incident response priorities.
Functional risks (top down): By systematically going through a framework and including the clauses/controls which apply to your business, you’ll get a great first pass at capturing all the risk titles you need with a simple re-word. e.g. taking NIST CSF as an example:
NIST PR.AT: Educate and train organisation personnel and partners to perform their cybersecurity-related duties and responsibilities as necessary based on related policies, procedures, and agreements,
becomes:
Unable to effectively educate and train personnel to perform their cybersecurity-related duties leading to greater chances of human error and social engineering and slower incident reporting.
Doing this for all those apply will give you risk headings for a fairly comprehensive register.
Stay tuned for Part 2 of this blog post when we tackle the remaining four steps of my BS-free cyber-risk management guide.
 This article is part of our ‘No bullshit cyber blog’ series, written by Assured CISO in residence, Nick Harris. “These blogs are designed to offer useful tips for implementing cybersecurity practice. The series focuses on making a difference in a language the business understands,” explains Harris. “All points are drawn from my personal experiences delivering cybersecurity transformation programmes and consider best practices from other industries. While I’ve had great success with these methods, you may have a better way. Apply what works for you, and let me know your suggestions.”
This article is part of our ‘No bullshit cyber blog’ series, written by Assured CISO in residence, Nick Harris. “These blogs are designed to offer useful tips for implementing cybersecurity practice. The series focuses on making a difference in a language the business understands,” explains Harris. “All points are drawn from my personal experiences delivering cybersecurity transformation programmes and consider best practices from other industries. While I’ve had great success with these methods, you may have a better way. Apply what works for you, and let me know your suggestions.”